| Package Data | |
|---|---|
| Maintainer Username: | xdroidteam |
| Maintainer Contact: | info@xdroid.com (Xdroid KFT.) |
| Package Create Date: | 2016-10-15 |
| Package Last Update: | 2026-01-26 |
| Language: | PHP |
| License: | MIT |
| Last Refreshed: | 2026-02-02 03:06:46 |
| Package Statistics | |
|---|---|
| Total Downloads: | 8,418 |
| Monthly Downloads: | 197 |
| Daily Downloads: | 1 |
| Total Stars: | 4 |
| Total Watchers: | 0 |
| Total Forks: | 0 |
| Total Open Issues: | 0 |
Add the following line to your composer.json (Laravel 5.4 and below):
"xdroidteam/xtrust": "0.1.*"
Add the following line to your composer.json (Laravel 5.5):
"xdroidteam/xtrust": "0.2.*"
Then run composer update.
or you can run the composer require command from your terminal:
composer require xdroidteam/xtrust
Then in your config/app.php add to the providers array:
XdroidTeam\XTrust\XTrustServiceProvider::class,
and to aliases array:
'XTrust' => XdroidTeam\XTrust\XTrust::class,
If you are going to use Middleware (requires Laravel 5.1 or later) you also need to add
'permission' => \XdroidTeam\XTrust\Middleware\XTrustPermissionMiddleware::class,
to routeMiddleware array in app/Http/Kernel.php.
Deploy migration file:
php artisan vendor:publish --tag=xdroidteam-xtrust
You may now run it with the artisan migrate command:
php artisan migrate
Create a Role model inside app/models/Role.php using the following example:
<?php namespace App\Models;
use XdroidTeam\XTrust\Models\XTrustRole;
class Role extends XTrustRole
{
...
}
Create a Permission model inside app/models/Permission.php using the following example:
<?php namespace App\Models;
use XdroidTeam\XTrust\Models\XTrustPermission;
class Permission extends XTrustPermission
{
...
}
Next, use the XTrustUserTrait trait in your existing User model. For example:
<?php
use XdroidTeam\XTrust\Traits\XTrustUserTrait;
class User extends Eloquent
{
use XTrustUserTrait; // add this trait to your user model
...
}
Don't forget to dump composer autoload
composer dump-autoload
There are roles and permissions. You can attach many permissions to a role, and attach many roles to a user, like in Zizaco/entrust. The main difference, that you can directly attach or detach permissions to a user.
You have four permissions:
You have two roles, with permissions:
You have two users, with roles:
If you don't want Adam Admin, to be able to delete, you can simply detach the can_delete permission from him. The admin group can still have the can_delete permission, but Adam will not. If you want Super User to be able to edit, you can attach this permisson (can_edit) to her. The other users in the user role will still be unable to edit, except her.
Because of this logic, you can't check the user roles, only the permissions!
Example for UI:
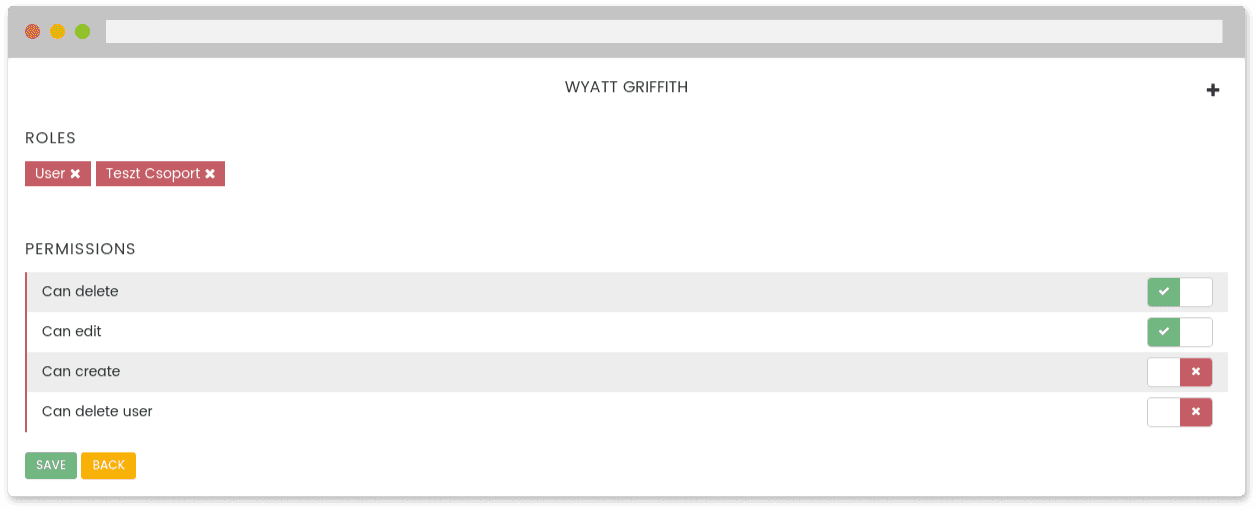
Check one permission:
XTrust::hasPermission('can_delete');
Returns true, if the authanticated user has the permission, returns false if not.
Check multiple permissions:
XTrust::hasPermissions(['can_delete', 'can_edit']);
Returns true, if the authanticated user has all the permissions, returns false if not.
Or:
XTrust::hasOneOfPermissions(['can_delete', 'can_edit']);
Returns true, if the authanticated user has one of the permissions, returns false if not.
You can also check within the user model:
$user = User::find(1);
$user->hasPermission('can_delete');
// OR
$user->hasPermissions(['can_delete', 'can_edit']);
// OR
$user->hasOneOfPermissions(['can_delete', 'can_edit']);
Route::group(['middleware' => ['auth', 'permission:can_show']], function(){
Route::get('/', 'HomeController@index');
});
For multiple permission check use pipe symbol as OR operator:
Route::group([
'middleware' => [
'auth',
'permission:can_show|can_create|can_edit|can_delete'
]
], function(){
Route::get('/admin', 'AdminController@index');
});
To emulate AND functionality just use multiple instances of middleware For multiple permission check use pipe symbol as OR operator:
Route::group([
'middleware' => [
'auth',
'permission:can_show',
'permission:can_create'
]
], function(){
Route::get('/admin', 'AdminController@index');
});
@permission('can_delete')
{!! Form::open([
'url' => '/users/'.$user->id,
'method'=> "DELETE"
] ) !!}
<button class="btn btn-sm btn-danger">
Delete
</button>
{!! Form::close() !!}
@endpermission
Multiple permissions:
@permissions(['can_show', 'can_delete'])
<span>Something</span>
@endpermissions
Returns true, if the authanticated user has all the permissions, returns false if not.
Or:
@oneofpermissions(['can_show', 'can_delete'])
<span>Something</span>
@endoneofpermissions
Returns true, if the authanticated user has one of the permissions, returns false if not.
Check one role:
XTrust::hasRole('can_delete');
Returns true, if the authanticated user has the role, returns false if not.
Check multiple roles:
XTrust::hasRoles(['can_delete', 'can_edit']);
Returns true, if the authanticated user has all the roles, returns false if not.
Or:
XTrust::hasOneOfRoles(['can_delete', 'can_edit']);
Returns true, if the authanticated user has one of the roles, returns false if not.
You can also check within the user model:
$user = User::find(1);
$user->hasRole('can_delete');
// OR
$user->hasRoles(['can_delete', 'can_edit']);
// OR
$user->hasOneOfRoles(['can_delete', 'can_edit']);
Always use the the id of the role or permission for attaching/detaching!
Attach one role to a user:
$user->attachRole(1);
Attach multiple roles to a user:
$user->attachRoles([1,2]);
Attach one permission to a user:
$user->attachPermission(1);
Attach multiple permissions to a user:
$user->attachPermissions([1,2]);
Detach one role from a user:
$user->detachRole(1);
Detach multiple roles from a user:
$user->detachRoles([1,2]);
Detach one permission from a user:
$user->detachPermission(1);
Detach multiple permissions from a user:
$user->detachPermissions([1,2]);
Attach one permission to a role:
$role->attachPermission(1);
Attach multiple permissions to a role:
$role->attachPermissions([1,2]);
Detach one permission from a role:
$role->detachPermission(1);
Detach multiple permissions from a role:
$role->detachPermissions([1,2]);